IN THE NEWS...
ARTICLES
THE VIDEO STORAGE PROBLEM
Michele Hope April 11, 2018
Technology now allows the capture of sharper, crisper IP video surveillance footage. But, such technical advances come at a cost — especially in terms of the investment in video surveillance storage now required to support the centralized storage, analysis and retrieval of an organization’s growing mountain of video footage.
So, which industries deal with the issue of video surveillance storage? And, how much storage is needed?
For the first question, just think of the world you pass through: traffic intersections, freeways, banks, airports, train stations, sports arenas, parking lots, public buildings, public spaces, retail stores, corporate buildings, hospitals and police departments (with dashboard cams and/or body-worn cameras). You are likely to encounter surveillance cameras with most of these locations. Each camera “feed” must then be digitally stored for a matter of days, weeks, months or, sometimes, years.
The question about needed capacity is harder to answer. Things to consider include the frames per second (fps) you record, the compression used, the number of cameras/video streams and your retention requirements. Don’t be surprised when a half-hour of surveillance video needs several hundred megabytes of storage. Seagate (and a Cisco IP video surveillance planning guide) offer some calculation examples.
The question of retaining surveillance video relates to governmental and industry regulations, codes and court cases surrounding compliance, privacy, long-term retention and the use of captured surveillance video. Here’s just a taste of three retention trends:
-
Banks: ATM security footage is retained for an average of six months, with some banks and countries requiring more or less, according to Reolink. (The United Arab Emirates bank must retain its security footage for one year.)
-
Washington, D.C. Metropolitan Police Department (MPD): Body-worn camera (BWC) surveillance videos that do not contain a crime are retained for 90 days; videos associated with a citizen’s complaint are retained for 5-10 years; videos subject to FOIA requests are retained indefinitely.
-
Retail/Private Entities: According to Mike Bomas, senior advisor of strategy and corporate planning at Viotaas, retention lengths vary depending on lawyer counsel, the likelihood of security risk or, in the case of future retail “slip-and-fall” cases, the probability footage may be needed for a dispute.
The growing CapEx costs to store surveillance footage has caused many organizations to look for other options. What about emerging cloud storage services for long-term video surveillance? Can they offer a more viable, fixed monthly amount to such costly CapEx spend?
Some services may integrate with popular video management system solutions. Others may even offer tiering of video data to different types of storage, such as disk, tape or both. Consider asking cloud providers how these services stack up against on-premises retention — in terms of TCO, access, chain-of-custody, compliance, privacy and your needs for long-term retention.



In the world of embedded and computer security, one of the often debated topics is whether 128-bit symmetric key, used for AES (Advanced Encryption Standard) is computationally secure against brute-force attack. Governments and businesses place a great deal of faith in the belief that AES is so secure that its security key can never be broken, despite some of the inherent flaws in AES.
This article describes the strength of the cryptographic system against brute force attacks with different key sizes and the time it takes to successfully mount a brute force attack factoring future advancements in processing speeds.
Any cryptographic algorithm requires multi-bit key to encrypt the data as shown in Figure 1.
Figure 1: Multi-bit key to encrypt data using cryptographic algorithm
The key length used in the encryption determines the practical feasibility of performing a brute-force attack, with longer keys exponentially more difficult to crack than shorter ones.
Brute-force attack involves systematically checking all possible key combinations until the correct key is found and is one way to attack when it is not possible to take advantage of other weaknesses in an encryption system.
Here is an example of a brute force attack on a 4-bit key:
Figure 2: Brute Force attack on 4-bit key
As shown, it will take a maximum 16 rounds to check every possible key combination starting with "0000." Given sufficient time, a brute force attack is capable of cracking any known algorithm.
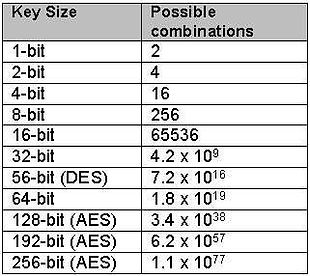
The following table just shows the possible number of key combinations with respect to key size:
Figure 3: Key combinations versus Key size
Notice the exponential increase in possible combinations as the key size increases. "DES" is part of a symmetric cryptographic algorithm with a key size of 56 bits that has been cracked in the past using brute force attack.
There is also a physical argument that a 128-bit symmetric key is computationally secure against brute-force attack. Just consider the following:
Faster supercomputer (as per Wikipedia): 10.51 Pentaflops = 10.51 x 1015 Flops [Flops = Floating point operations per second]
No. of Flops required per combination check: 1000 (very optimistic but just assume for now)
No. of combination checks per second = (10.51 x 1015) / 1000 = 10.51 x 1012
No. of seconds in one Year = 365 x 24 x 60 x 60 = 31536000
No. of Years to crack AES with 128-bit Key = (3.4 x 1038) / [(10.51 x 1012) x 31536000]
= (0.323 x 1026)/31536000
= 1.02 x 1018
= 1 billion billion years
Figure 4: Time to crack Cryptographic Key versus Key size
As shown above, even with a supercomputer, it would take 1 billion billion years to crack the 128-bit AES key using brute force attack. This is more than the age of the universe (13.75 billion years). If one were to assume that a computing system existed that could recover a DES key in a second, it would still take that same machine approximately 149 trillion years to crack a 128-bit AES key.
There are more interesting examples. The following snippet is a snapshot of one the technical papers from Seagate titled "128-bit versus 256-bit AES encryption" to explain why 128-bit AES is sufficient to meet future needs.
If you assume:
-
Every person on the planet owns 10 computers.
-
There are 7 billion people on the planet.
-
Each of these computers can test 1 billion key combinations per second.
-
On average, you can crack the key after testing 50% of the possibilities.
Then the earth's population can crack one encryption key in 77,000,000,000,000,000,000,000,000 years!
The bottom line is that if AES could be compromised, the world would come to a standstill. The difference between cracking the AES-128 algorithm and AES-256 algorithm is considered minimal. Whatever breakthrough might crack 128-bit will probably also crack 256-bit.
In the end, AES has never been cracked yet and is safe against any brute force attacks contrary to belief and arguments. However, the key size used for encryption should always be large enough that it could not be cracked by modern computers despite considering advancements in processor speeds based on Moore's law.
About the author
Mohit Arora (mohit.arora@freescale.com) is a Sr. Systems engineer and Security Architect at Freescale Semiconductor. He is responsible for product and architecture definition for 32-bit industrial and general-purpose parts. "Embedded Security" is one of his main expertise and focus areas and he also leads the Security IP Asset team in AISG (Automotive Industrial and Solution Group). He holds more than 35 publications and is also the author of the book "The Art of Hardware Architecture."